
Borat, a new remote access trojan (RAT) with easy-to-use capabilities has emerged on the darknet markets. The malware focuses on DDoS (Distributed-Denial-of-Service) cyberattacks, ransomware distribution, and UAC bypass.
How Does Borat Work?
Borat is a RAT that allows remote hackers to be in full control over their targets’ mouse and keyboard, and access files, and network points while concealing their presence.
The threat actors who leverage it can customize their compilation options for compact payloads building purposes. These payloads fit the requirements necessary to conduct cyberattacks that are highly tailored.
The ones who discovered Borat were the experts from Cyble, who managed to sample the malware for a technical investigation that demonstrated its operation and published a report on this topic.
A Remote Access Trojan or RAT is a tool used by Threat Actors (TAs) to gain full access and remote control on a user’s system, including mouse and keyboard control, files access, and network resources access. During our regular OSINT research, Cyble Research Labs came across a new Remote Access Trojan (RAT) named Borat. Unlike other RATs, the Borat provides Ransomware, DDOS services, etc., to Threat Actors along with usual RAT features, further expanding the malware capabilities. The developer named this RAT ‘Borat’ after a black comedy mockumentary film, and the photo used in the RAT is of actor Sacha Baron Cohen, who played the main role in the film Borat.
What Features Does Borat Have?
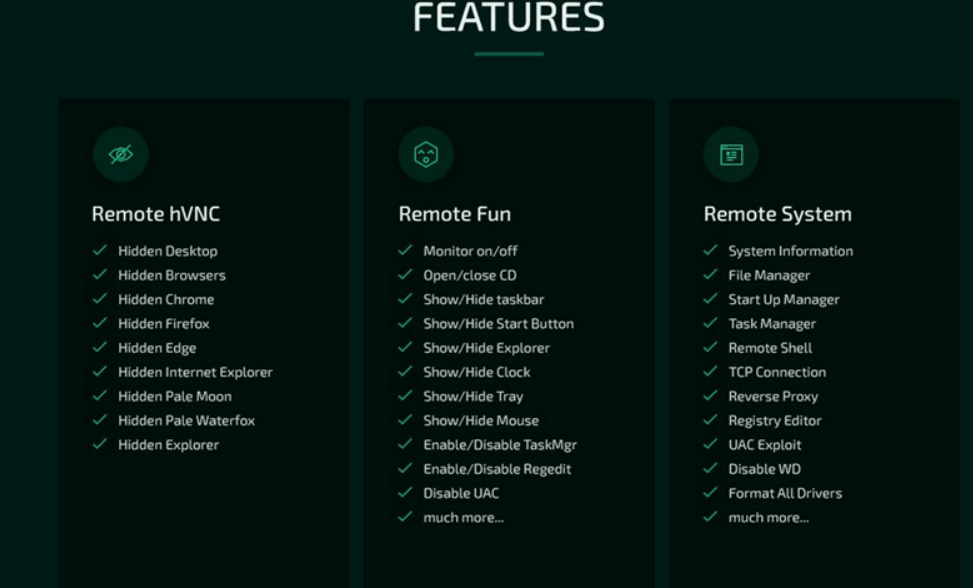
The fact that whether the RAT under discussion is distributed for free among threat actors or it’s being put up for sale is unclear at the present moment. Researchers from Cycle underlined some features of Borat they identified:
Keylogging
This feature has the role to keep track of key presses. These will be stored in a text file.
Ransomware Deployment
Borat can be used to deliver ransomware payloads to the victim’s computer and automatically create a ransom note.
Serving for DDoS Cyberattacks Purposes
The RAT redirects trash traffic to a target server utilizing the resources of the hacked system.
It Has Sound and Camera Recording Functionalities
If a microphone is available, Borat records audio through it and saves it as a wav file. If a webcam is accessible, footage from it will be recorded.
Remote Desktop Feature
This feature indicates that the RAT can start a secret remote desktop for file operations, access input devices, run code, open programs purposes, and more.
Reverse Proxy Functionality
This feature puts up reverse proxy to protect the remote operator’s identity from being revealed.
It Can Collect Device Info
It can obtain basic system information by gathering device information.
Process Hollowing Capability
Process hollowing is when malware is injected into legitimate processes for detection evasion purposes.
It Can Steal Credentials
Borat can perform credential theft from Chromium-based web browsers and also steal discord tokens from the targeted users.
Besides these main above itemized features, other functions include playing audio, swap mouse buttons, hiding the desktop, hiding the taskbar, holding the mouse, turning off the monitor, showing a blank screen, or hanging the system to confuse and disrupt the victim.
What do the listed features indicate is the fact that Borat is effectively a RAT, spyware, and ransomware, as Cyble experts emphasize, so it’s a formidable threat that can perform a range of destructive activities on a system.
According to BleepingComputer, threat actors typically disseminate these tools through laced executables or files masquerading as cracks for games and programs, so avoid downloading anything from untrustworthy sources like torrents or dodgy websites.
About Remote Access Trojans
As we described in a past article, remote access trojans represent a form of malware that allows an attacker to take complete control of your computer remotely. By means of a remote access trojan, threat actors can effortlessly gain access to your local files, secure login authorization, and other sensitive information, as well as the ability to exploit that connection to download infections that you might unwittingly spread to others.
How Can Heimdal™ Help
To protect against RATs, you must have the proper cyberssec solutions put in place. Use our Threat Prevention, an astonishing DNS filter that prevents data leakage, and ransomware by using advanced DNS, HTTP, and HTTPS filtering analysis for every endpoint you have.
